We have received several requests around video conferencing solutions over the past few weeks. While the official OIT conferencing solution is currently Skype For Business, we have received the most requests about Zoom.
Zoom is indeed a very easy to use solution that offers free conferences for up to 40 minutes as well as paid unlimited plans.
Is Zoom Secure?
Zoom has received several security criticisms recently due to enormous demand and usage during the COVID-19 crisis. The FBI has issued warnings around Zoom and several Philadelphia government agencies are currently restricting its use. However, Zoom and other outlets have released several guidelines on how to secure your Zoom conferences if you are the host.
Recommended Zoom Settings
Before the Meeting
When you log into the Zoom website, you can select the settings by clicking “Settings” on the left hand side of your profile. You will need to configure these setting from the web site and not the client on your computer.
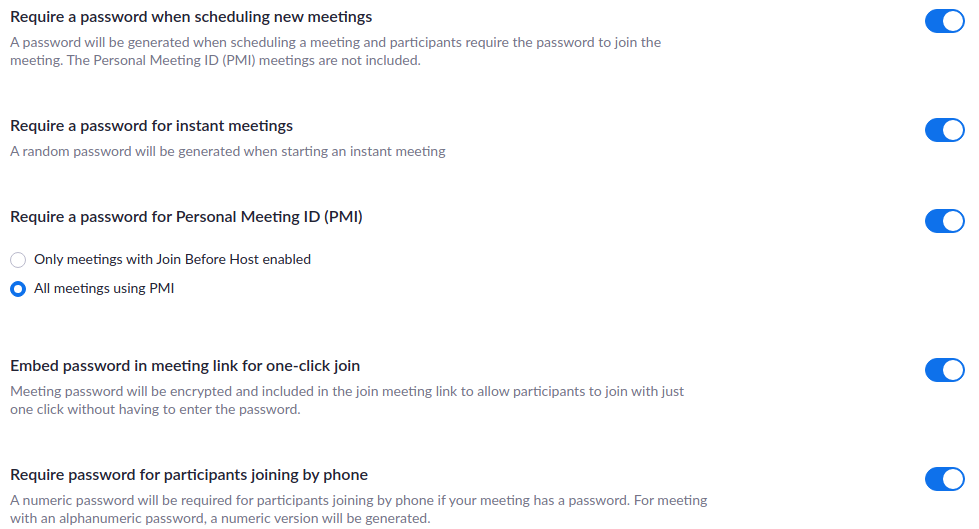
Password protect your meetings
This setting prevents malicious users from guessing your meeting ID. There are a few locations where a password should be set.
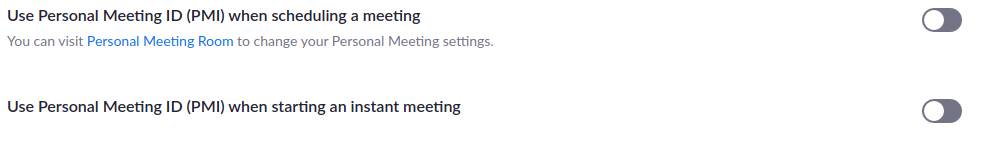
Use a randomly generated meeting ID
By default, Zoom will give you a personal meeting ID that does not change. Anyone who would have joined your meeting previously would always know your personal meeting ID in the future and could join accidentally or maliciously. To add some confusion, this is a setting you turn off rather than on.
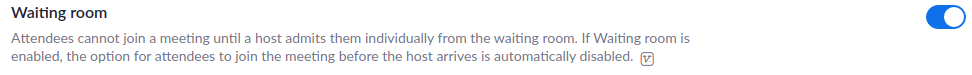
Do not allow participants to join before the host
This gives the host of the meeting the greatest control to see participants before they can interact with other participants.

There is also a waiting room feature that you can enable to have individual control of admitting each user.
In Meeting Controls
While you are in a meeting there are several security controls you have to oversee your meeting. To access them, float your mouse over the bottom of the meeting screen to show the toolbar. From the toolbar, select the Security icon.
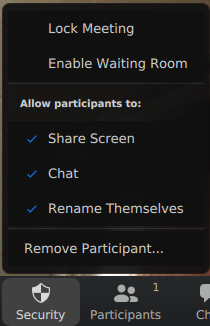
Lock your meeting
Once your meeting has started and you are sure all of the participants you are expecting have joined, lock your meeting. Now new and uninvited guests cannot join.
Turn off Screen sharing
If you do not expect participants to share something then turn this off. Many security warnings of “Zoom bombing” are happening because users share something unwanted.
A Note on Privacy
Please keep in mind your surroundings as well as everyone else in your meeting especially if your meeting needs to contain personal or health related information. If you intend to use the meeting for this purpose especially HIPAA information, please check with your HIPAA privacy officer for guidance.
More Information
For more information, see Zoom’s web site where they have several other security recommendations.
— Update: January 21, 2022 —
Enabling end-to-end encryption for meetings
End-to-end (E2EE) encryption for meetings is now available. Account owners and admins can enable end-to-end encryption for meetings, providing additional protection when needed. Enabling end-to-end encryption for meetings requires all meeting participants to join from the Zoom desktop client, mobile app, or Zoom Rooms.
To enable End-to-end (E2EE) encrypted Zoom meetings for all users in the account:
- Sign in to the Zoom web portal as an admin with the privilege to edit account settings.
- In the navigation panel, click Account Management then Account Settings.
- Click the Meeting
- Under Security, verify that Allow use of end-to-end encryption is enabled.
- If the setting is disabled, click the toggle to enable it. If a verification dialog displays, click Turn On to verify the change.
- (Optional) If you want to make this setting mandatory for all users in your account, click the lock icon, and then click Lock to confirm the setting.
- Under Security, choose the Default encryption type.
- Click Save.
- Note: Because of the limitations of E2EE, we recommend using Enhanced encryption as the default encryption type and using end-to-end encryption for meetings where additional protection is required.
More Information
For more information, see Zoom’s End-to-end encryption support article where they have several other security recommendations.
